Cyber
PROTECTION
Automatized Sagenso system provides your company with 24/7 security all year round!

Advanced prediction of cyberthreats
We ensure safety from threats to your organization coming from both outside and inside. Thanks to the Sagenso system:
PREDICT
Reveal the vulnerabilities of your IT infrastructure (before others do)
Automated monitoring of the IT environment configuration shows the user where potential vulnerabilities can be found, how to deal with them and if the actions taken are sufficient. From this moment on you will not be wasting any time to find out how to efficiently protect your servers, workstations and other office appliances on your own.
REACT
Gain time and react efficiently
Sagenso analyses the events from the IT infrastructure on its own, both those initiated by the services as well as those initiated by the users. As soon as there are any changes or potentially dangerous behaviours detected, you will be alerted immediately through communication channels of your own choosing.
.jpg)
.jpg?width=2564&name=scrin2%20(1).jpg)
IMPROVE
Manage whenever you are needed
IT security does not only include infrastructure, systems and applications. Sagenso internal audit system monitors the completion progress of tasks, processes and practices related to IT security requited in your organization. You will never forget about anything / nothing will go unaddressed / you will have control over everything.
LET'S make IT SECURE
Your monitoring centre

NEXT-GEN CYBERSECURITY SOLUTIONS
Effective and straightforward security management
- IT Infrastructure
- Accounts
- CERT
- Vulnerabilities
- Passwords
- Backup
- User profiles
- Tasks
- KPIs
- Reports
- Architecture
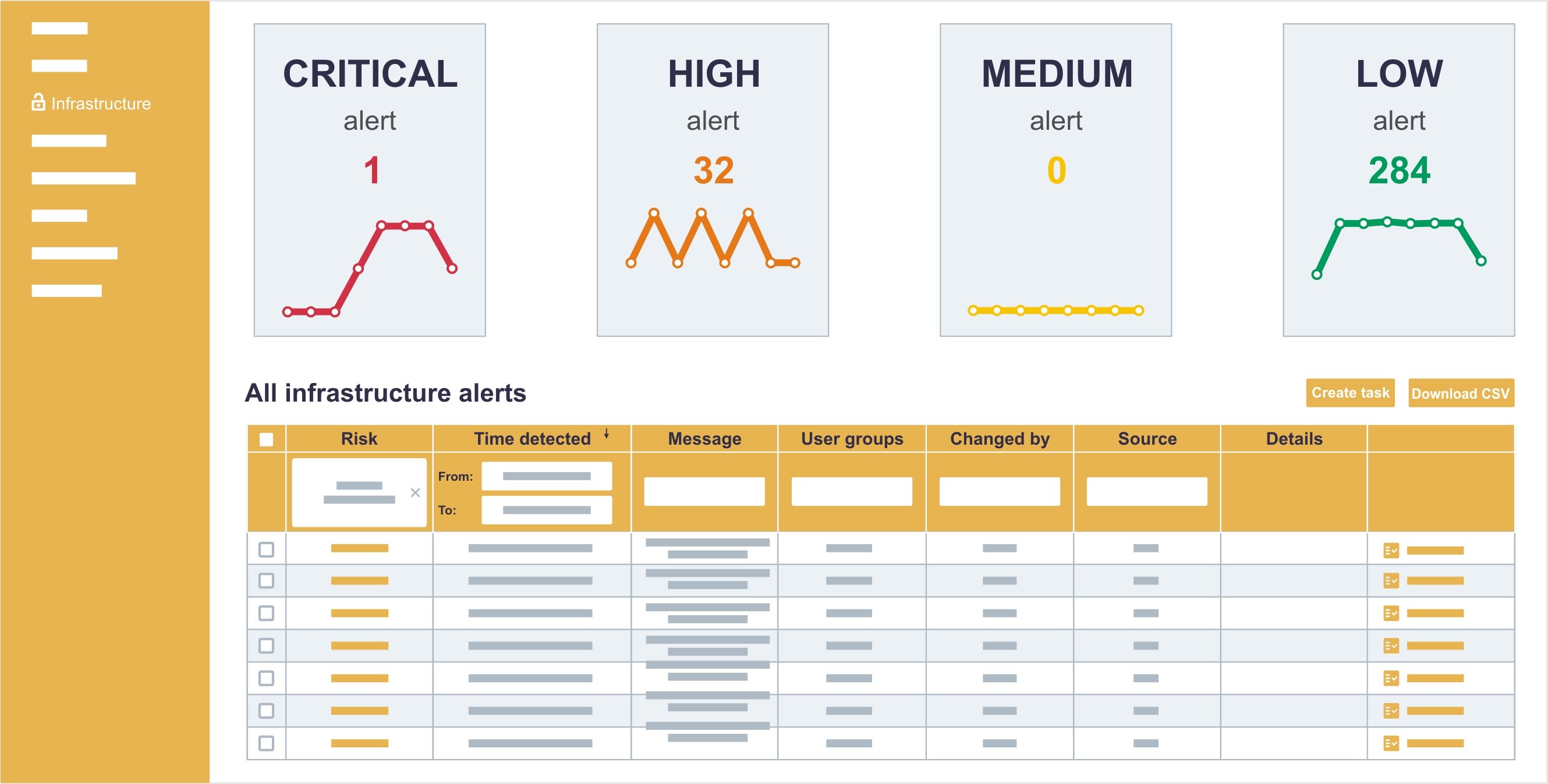
IT infrastructure monitoring
Sagenso, through integration with various information sources (e.g., registers, events logs), analyses the IT services configuration with good practices in mind as well as to identify potential anomalies which would impact the overall IT security level in the organization. Analysis considers current state as well as any future modifications to IT services configuration.
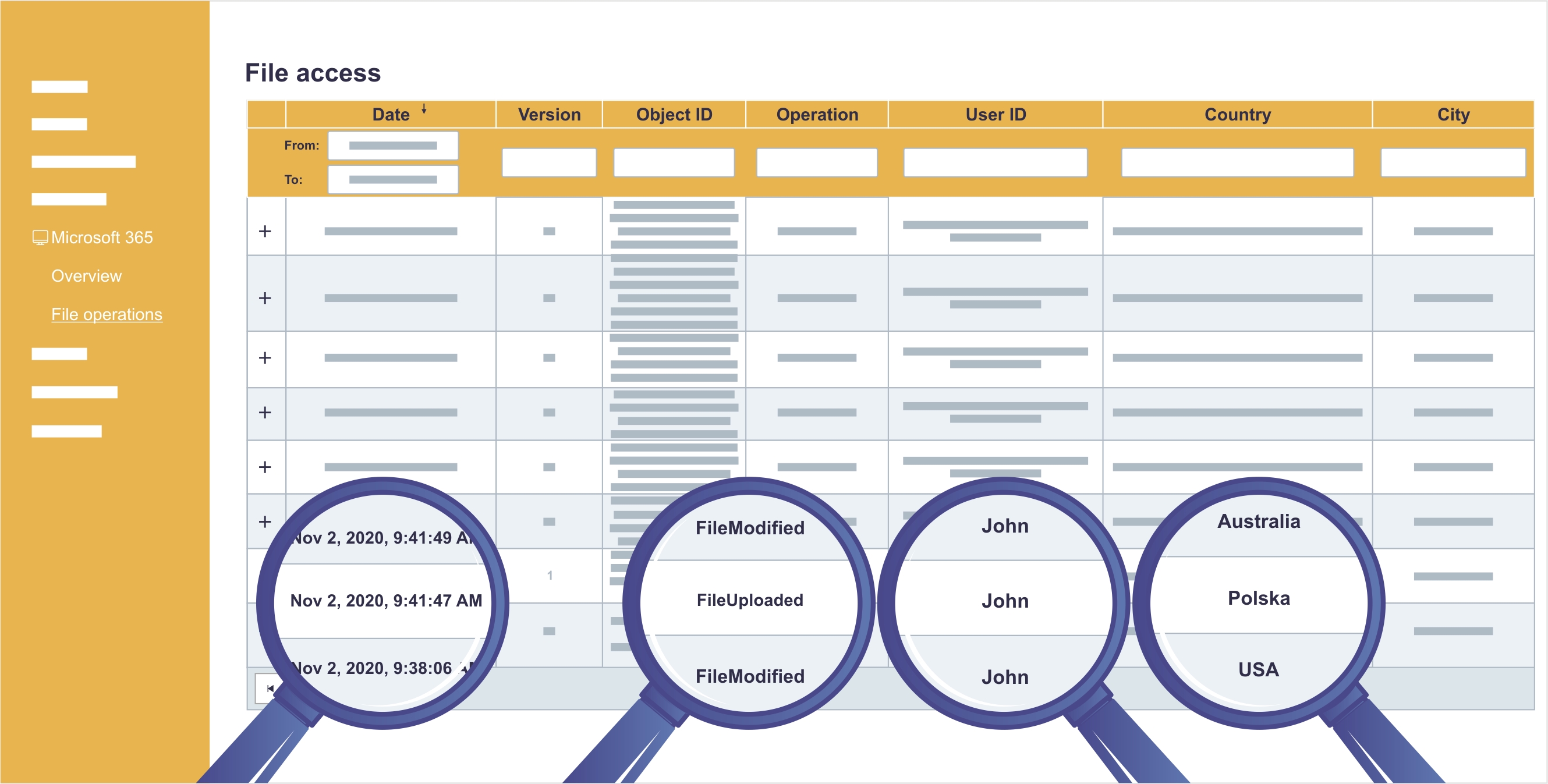
Accounts activity monitoring
The main cause of most of the cyberthreats are either conscious or accidental actions of IT services users. Sagenso analyses the activity of accounts in the system and relates them to already known patterns of attacks so the activity potentially threatening the security of your organization can be identified.
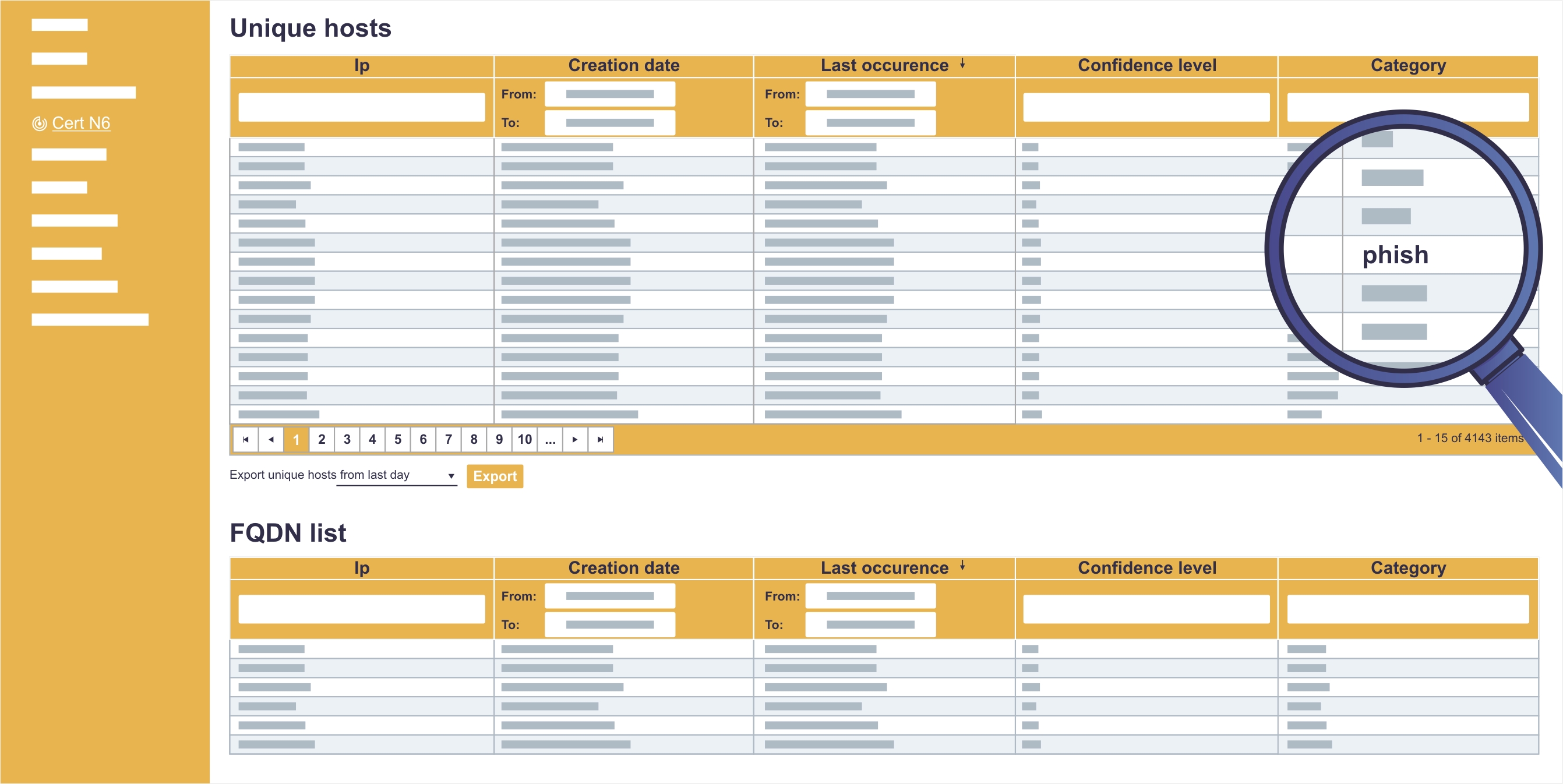
CERT integration
Knowledge about the newest attack methods is crucial for an effective security system. That is why the Sagenso system has integrated the CERT system made to exchange information about new threats both in Poland and around the world.
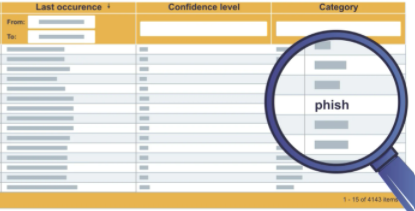
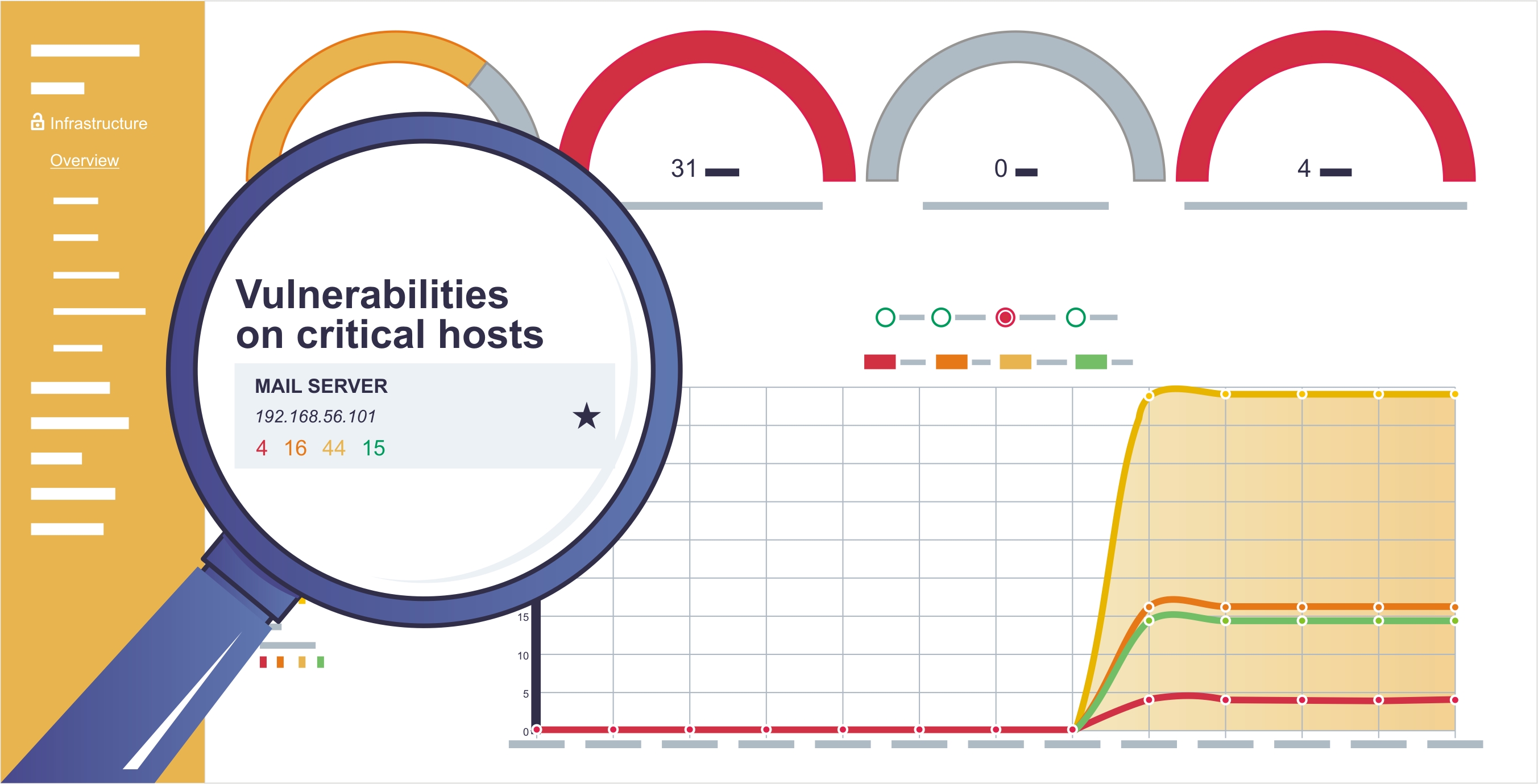
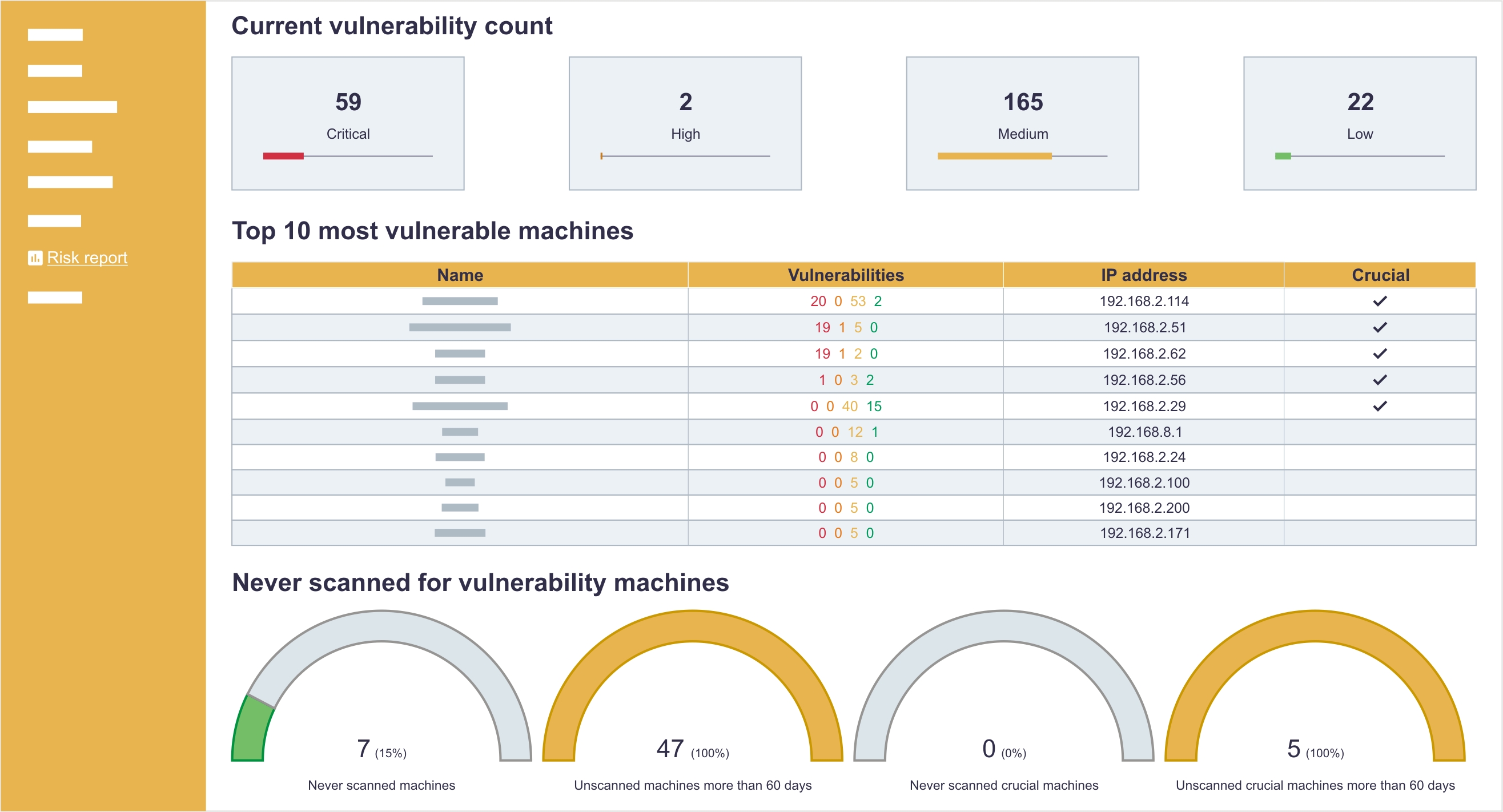
Vulnerabilities management
Because of Sagenso, your organization will receive not only the theoretical knowledge about potential vulnerabilities in your IT infrastructure but also will help you manage them effectively (e.g., get rid of vulnerabilities in accordance to the business’ priority or because of how easy it is to exploit specific vulnerability) and control the efficiency of corrective efforts.

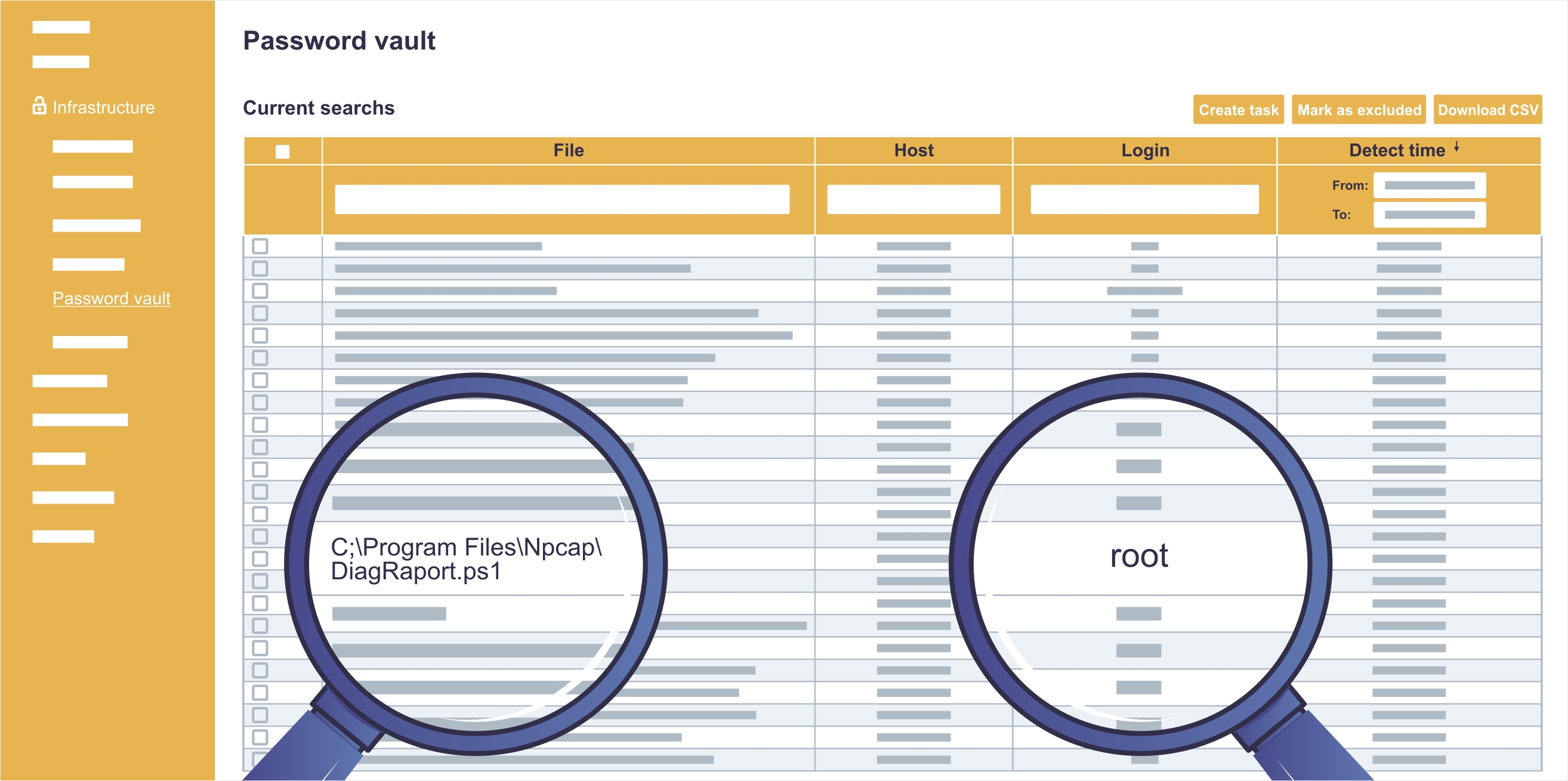
Scanning for overt passwords
The safety of privileged accounts (e.g., administrator, root) is the most critical point in the whole organization. Sagenso informs you about any scripts containing overt credential data.

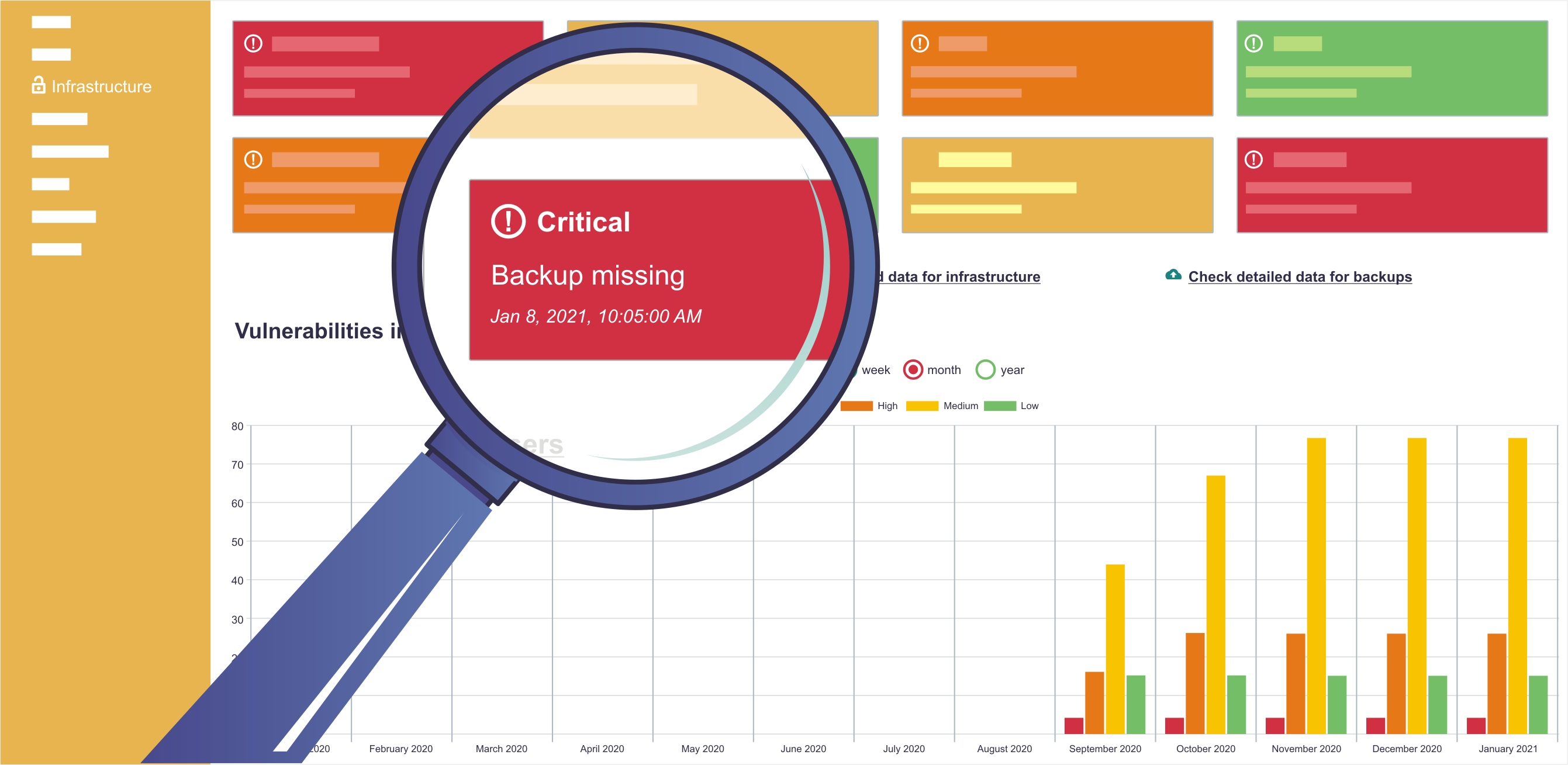
Backup configuration
One of the most fundamental aspects of IT security are backups. Sagenso can monitor the backup generation process in your organization and check if it is performed in accordance with the business expectations.
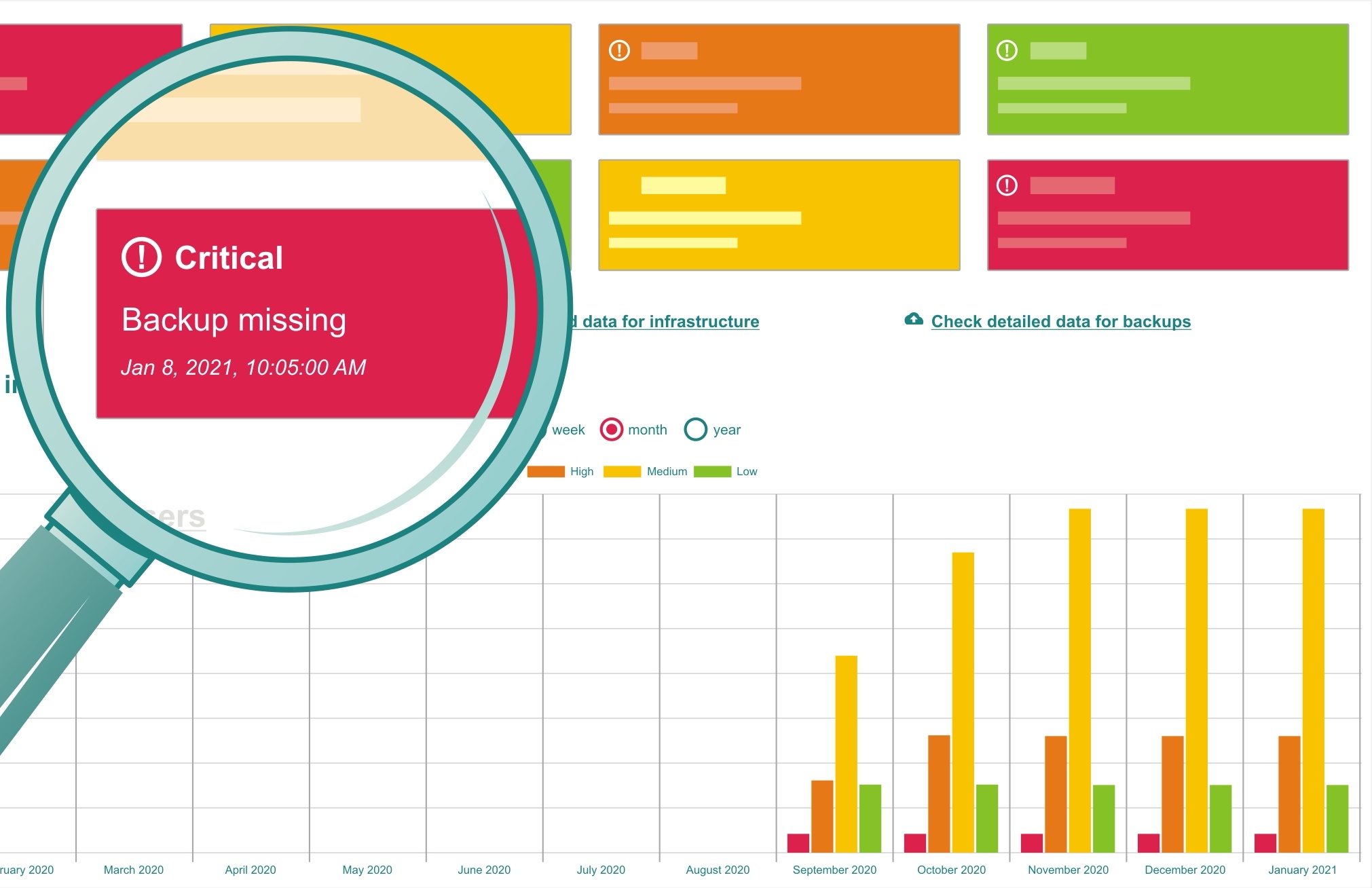
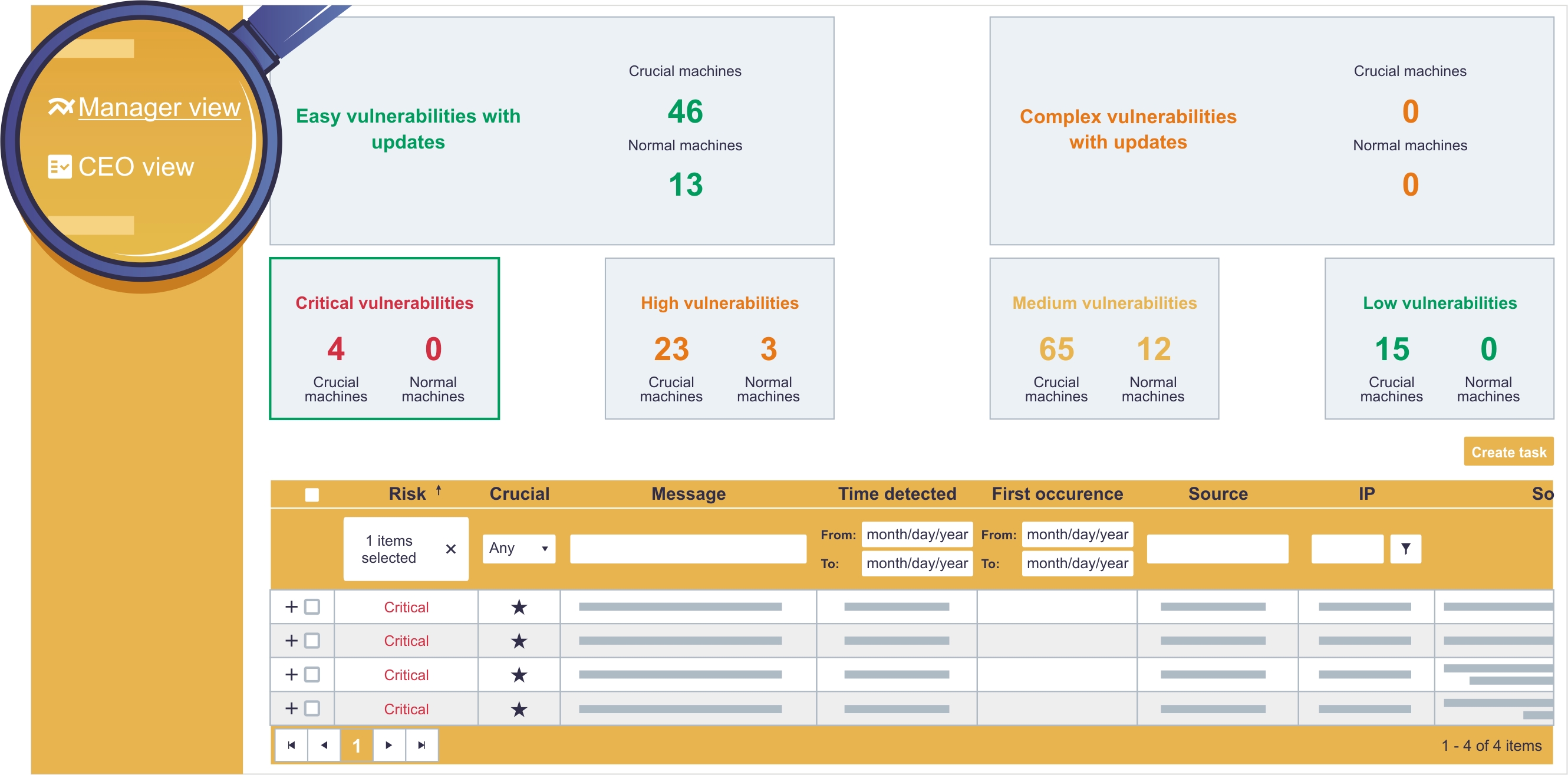
Profiles tailored to the user
Depending on your role in the organization and the information that is of interest to you, one of the three specific user profiles may be chosen. The profiles have been designed to present the required information in a clear manner for either a technician, a manager or a business owner.

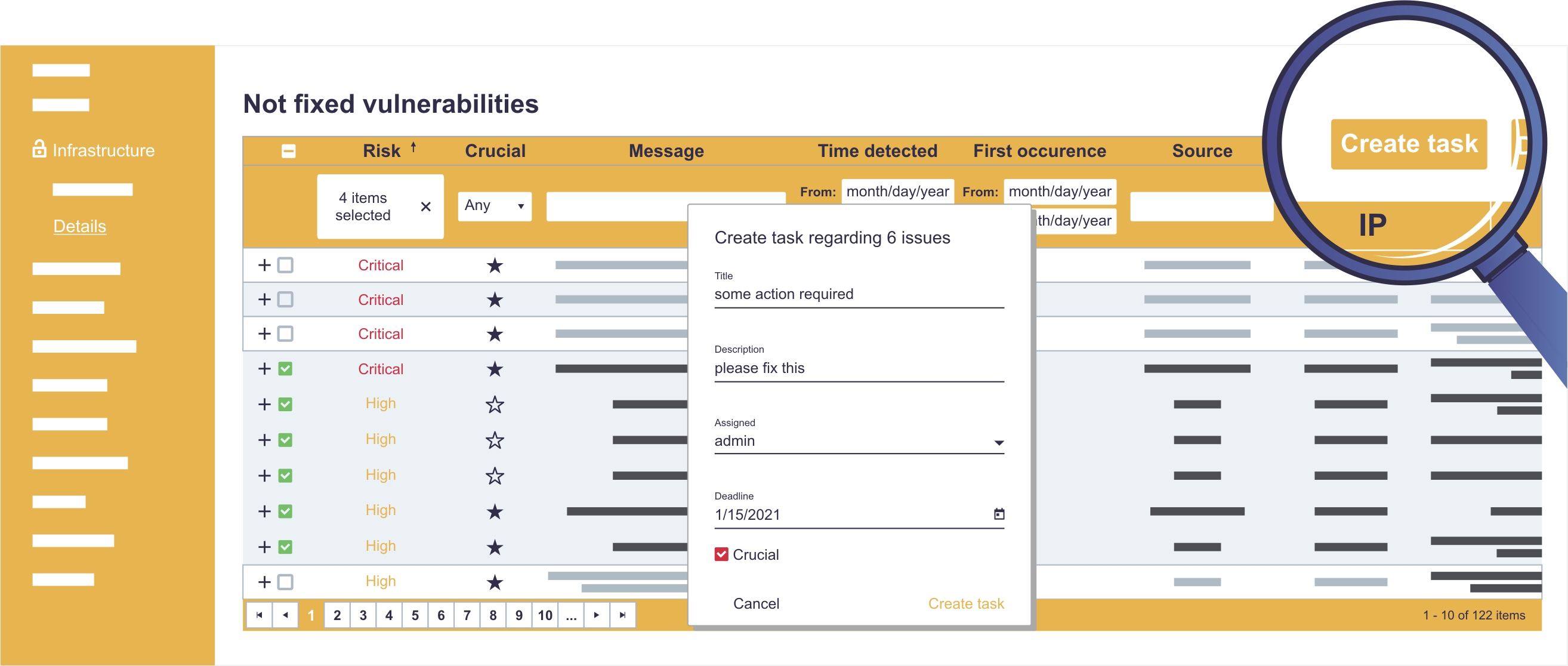
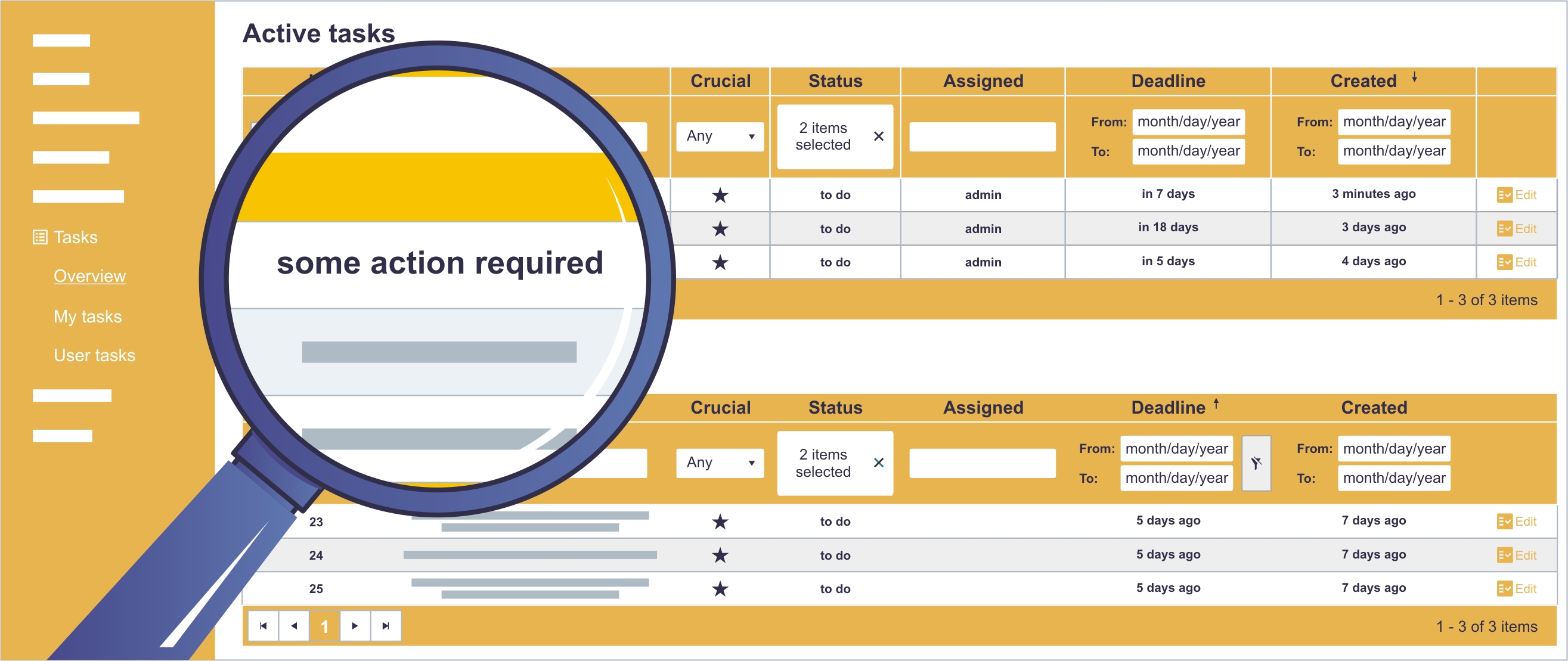
Tasks management
Sagenso has a built-in module to manage tasks regarding security. It lets you supervise the order and the completion of assigned tasks. It is not mandatory to use this feature, because some of the responsibilities can be taken care of by Sagenso itself and your involvement would be only necessary if appropriate escalation is required.

Processes monitoring and KPI
Beyond the world of technology, there is also a business aspect of IT security. That is why Sagenso automatically monitors and reports the key performance indicators in the cybersecurity administration field. You do not have to be an expert in IT security to see whether your organization is secured or not.
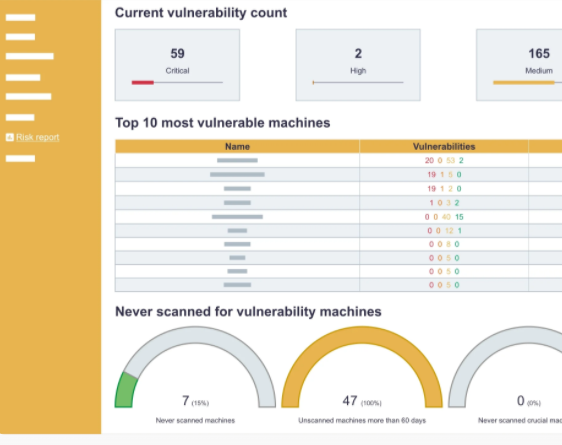
Reporting module
Sagenso has a report module that will update you with the most important information about the security of your organization in a form of reports that you can receive by a preferred communication medium in a selected timeframe. Even if you get overwhelmed with other aspects of your business, Sagenso will make sure that nothing important slips by you.
.jpg?width=2564&height=1621&name=scrin2%20(1).jpg)
Architecture
Sagenso has been designed in such a way to not only provide you with a reliable picture of the IT security in your organization but also to secure the data (e.g., events logs, system logs) which would be the most critical in case of an attack so as to find out what happened and how. Thanks to the architecture based on microservices this safety precaution can be scaled in accordance with your needs.
FREQUENTLY ASKED QUESTIONS
FAQ
We will provide you with support in every aspect of working with this tool. From implementation all the way to configuration and then the analysis of the collected. We are at your disposal.
How is the system implemented?
To prepare the environment for the implementation of the CyberStudio system, an access to a server with the Linux distribution system installed is required. The process of the CyberStudio installation itself is fully automated. For the system to be able to fulfil its role, an ActiveDirectory service account has to be created. In some cases two communication ports will have to be unlocked within the internal network.
What kind of data can be accessed by CyberStudio system administrators?
The support that we provide enables us to communicate only with the components inside the CyberStudio system composition, but only on previously agreed terms outlined by our clients. Even then any sensitive information will not be transferred anywhere outside of the monitored environment.
Does the CyberStudio system supervise the employees?
CyberStudio system was not created with supervising employees in mind. It only monitors the informational background created based on the user’s activity and the events initiated. For example, the system does not verify how much time an employee spends browsing websites, but it does check the reputation of public addresses in order to protect the infrastructure from potential threats.
What languages are supported by the system?
The system supports English and Polish.
Does an employee require any additional training to operate the system?
To use the CyberStudio system you do not require any additional training. The way of presenting the information in the system has been designed to be clear and understandable by both specified engineers and the general management team.
How much does it cost? One-time payment or fixed fee?
CyberStudio is sold as a yearly subscription and is mostly for small and medium-sized enterprises where employing a highly-trained cybersecurity expert is not an option.
How long does it take to implement CyberStudio system?
The time needed to implement CyberStudio system may vary based on the extent of the IT environment and the amount of data present in the events logs. Usually it takes around two to three hours to fully implement the system.
What threats does the system protect against?
The most important aspect of CyberStudio, which makes it stand out from any other similar system, is the analytical module collecting data from various elements of infrastructure and correlating it with potential cyberattack patterns. In essence, it means that even if some malicious software penetrates the antivirus protection, the CyberStudio system, using event context monitoring, will stop it effectively.
How often is the system being updated?
The system gets updated, on average, once a month. It is worth noting, however, that the updating process concerns every element of the CyberStudio system and the frequency of updates may be affected by, for example, information about the need for installation of a critical patch for the operating system on a hosting server.
What is the guarantee of the system's effectiveness?
Unfortunately, it is impossible (and probably never will be) to achieve 100% security in the world of cybersecurity. It is our main goal to use the most recent technological solutions as well as a native scientific background to share a security system with unprecedented effectiveness. Moreover, when you buy CyberStudio system, it includes high-quality insurance against cyberthreats.
Innovative analysis of security level
Threat Intelligence
We improve CyberStudio by regularly updating it and implementing new ideas, one of which being designing user specific profiles. This will help outlining unusual events which would suggest that one of the accounts has been compromised and a user is being impersonated by someone trying to acquire sensitive information.
Is Sagenso system for you??
If you run your own company, work as an IT manager, or process sensitive data – the answer is YES!
